
It’s about time!
Time is of the essence, timing is everything, be on time, don’t miss a deadline, I’m in a rush, there’s not enough time, I don’t have time for you.
In case you didn’t notice, this is all about TIME.
There are a lot of things to do with time that control our life, and we deal with it every day. This also applies for IT, and the way things work in the digital world. For instance, credit card transactions must be executed within 120 milliseconds to make sure the payment at the Point of Sale is working smooth, and a 0.5 second delay of a website will cause customers to be distracted while they wait longer for their turn, which can lead to the sales process not being completed .
But what does this have to do with Quantum technologies? Well . . . A lot!
To explain this, let’s look back at a little history of the internet. The Internet has grown from a few computers connected to each other with low-speed dialup phone lines in the 1960s to a global network of billions of people connected through medium speed and high-speed links that are reaching up to gigabits. Most of us can’t even imagine living our life without the Internet anymore. Just check the number of websites today at https://siteefy.com/how-many-websites-are-there/
But did you know that some technologies at the core of the Internet were created in the 70’s? TCP/IP (communication protocol) started in 1974 and in 1975 SMTP (email protocol) was introduced, and both are still being used today, albeit with additional ‘workarounds’ and ‘layers’ built on top of them to meet the current requirements regarding privacy and security.
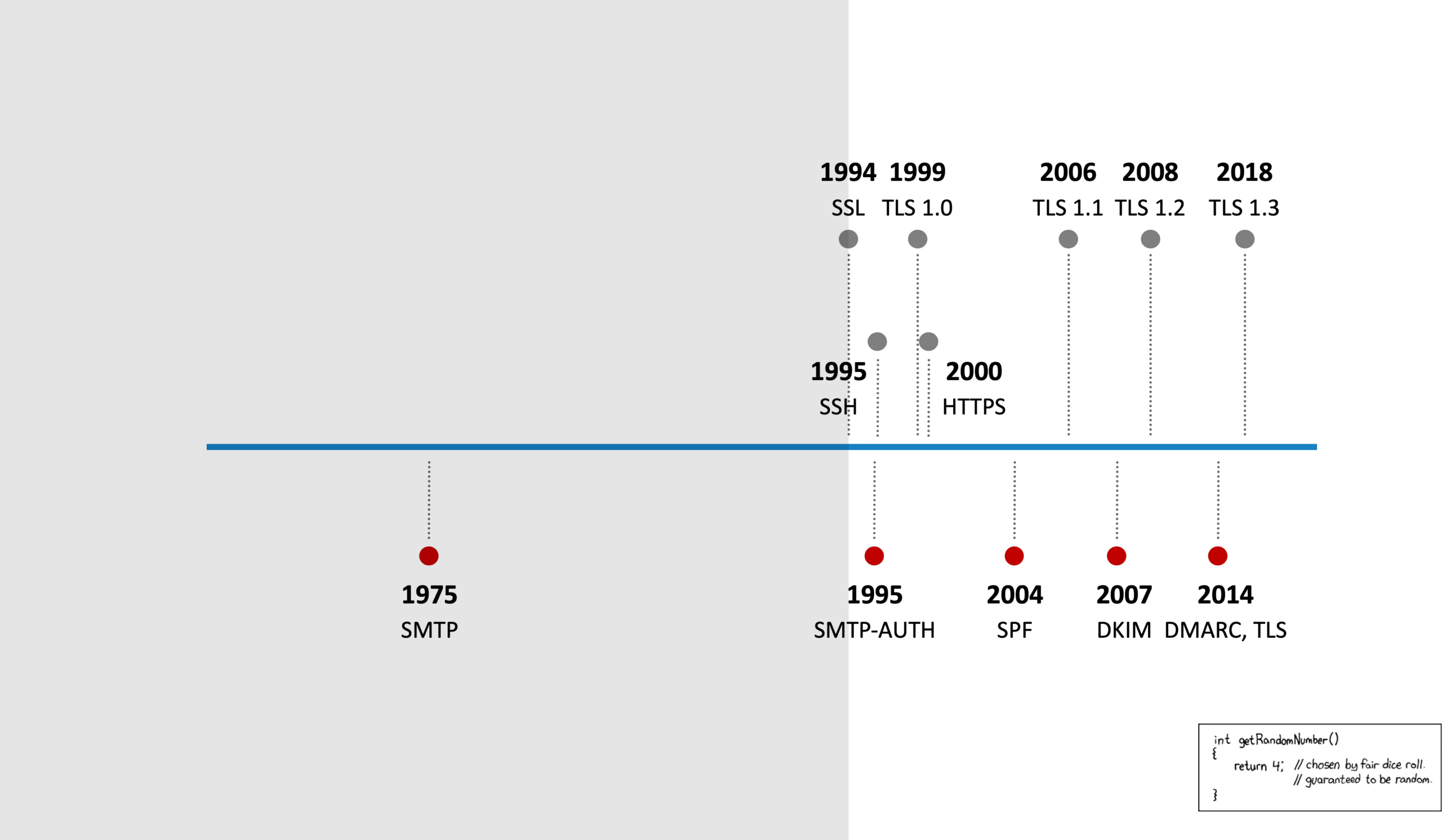
Depending on the usage, shortages and increasing importance of the Internet, we needed to add new and improved layers of technology to the Internet. This situation is similar to the introduction of SSL protocols in 1994, coincidentally the same year Peter Shor released Shor’s Algorithm, which will come back into play later (talking about time). Layer after layer was added, updates from our security protocols were created, until we reached the point that developing an application would need significant more time working on the non-core functionality resulting in the appearance of shortcuts in security functions due to the lack of time and/or expertise.
So today we’re already facing an Internet landscape consisting of more than 1 billion websites, almost 9 million apps, 200 million API backends, over 700 programming languages, more than 350.000 software libraries and 100+ ciphersuites to choose from.
And if you think that’s bad, just check the amount of usage of COBOL, one of the ancient programming languages used in more than 90% of Fortune 500 companies with over 30.000 organizations using it. And the thing is, nobody speaks COBOL anymore! So, if you need to update/upgrade such an application, how on earth are you going to do this?
And now Quantum, 1994, Peter Shor, Shor’s Algorithm, which constitutes a method for Quantum computers to easily find the prime factors of an integer, offering an exponential speedup compared to classical computing. So what, you might think? Well, this ‘hard’ problem for classical computing is the foundation for most of our existing asymmetric security protocols, and now suddenly it’s ‘easy’ for a Quantum computer! And these protocols are used in approximately 90% of all internet applications worldwide, and worse, in almost 100% of all your current mobile applications!
The reason why this can become a societal problem is due to two factors.
- The way our cyber security governance works.
- The way we consume news and information.
To make the story a little spicy, let’s call this scenario ‘The Quantum Apocalypse’.
Let’s pretend that at some point in time, let’s say 2035, there’s someone able to run Shor’s Algorithm on a medium sized (4000 logical qubits) Quantum computer and can break an RSA2048 keypair in a couple of hours, and they’re able to do this twice to demonstrate repeatability.
Why 2035? Well, according to a survey conducted by Dr. Michele Mosca there’s a 50% chance that this can happen in 2035, and if you look at the current developments of Quantum computers, this might well come true. It could also happen a few years later. Depending on who you ask, you might receive answers going for 2030, or up to 2045 or not at all.
When this happens, and they publish their results, the first main thing kicks in, meaning that when this happens, current asymmetric security protocols will be labeled as insecure. This will be followed by loads of regulations that state that regulated organizations must use security protocols that are either labeled ‘secure’ or ‘recommended’. Hence there will be an immediate need to upgrade all those applications.
And that’s not the worst part, because then the second factor comes into effect. When such a publication is made, news agencies will pick up this news, and some of them will create crazy headlines, like ‘The Internet is broken’ or ‘Our worst Quantum cybersecurity threat has come true’, to attract more customers to their websites to make money out of advertisements.
And then the real sh*t hits the fan when this publicity reaches social media. All kinds of people will share this, up to the moment that no-one is able to understand what really happens, and the only thing they read is that they can’t buy anything online anymore, and they can’t access their money with their mobile bank application anymore.
When this happens, people can only do one thing to get their money, which is run to an ATM machine and empty their bank account, and once this trend has started, it’s a matter of weeks before a complete collapse of our global economy could occur. Scared? Don’t worry, because we are working on solutions to prevent this scenario ever taking place, as we have developed quantum resilient solutions based on new protocols called Post Quantum Cryptography (PQC), which are security protocols that are resistant to this Quantum threat, and we are also developing communication technologies protected by quantum technology, to make online communication even more secure.
The thing is, to implement those new technologies, we need time .
Cryptography and security protocol upgrades in the past for large organizations usually took more than 10 years! And that was a regular drop-in replacement!
And finally, remember 2038? This is the year where the 32bit time counter ends, so we all need to make sure that all our applications are upgraded to 64bit. This has nothing to do with the Quantum threat, but it will require a huge number of resources as we’ve previously seen with Y2K. And we’re now facing a hundred times more applications and a larger code base. You will need to use automated tooling for your discovery and testing facilities.
So, what can you do now? Aren’t we already too late? Do we still have time? The answer is yes, we still have time, we are smart, we will produce solutions! But it is YOU who must act right now, as there is no vendor, consultant or other external party who has a full inventory of your cryptographic landscape, and that is where you need to start right now!
Find your partner and start your discovery of your landscape as a first step towards Quantum safe and enter your journey!
It’s TIME!
